What is digital forensics in forensic science?
Digital forensics plays a major role in forensic science. It’s a combination of people, process, technology, and law. Some notable methodologies are used to identify, collect, protect, preserve, analyze, extract, incident activity, recovery, and document a digital evidence report as per regional and international jurisdictions where the cybercrime occurred. Throughout the investigation data acquisition, data analysis, data integrity, data extraction, and reporting play a crucial role in the process.
The digital forensic industrial practices and services vary from one region to other regions across the globe. In 2012, ISO (the International Organization for Standardization) and IEC (the International Electrotechnical Commission) launched an ISO/IEC 27037:2012 common framework for Guidelines for identification, collection, acquisition, and preservation of digital evidence. Since then, different organizations frame their policies and implement them based on the Codes of Practice and Conduct for digital Forensic standards. There are some other notable ISO/IEC frameworks used in practice, such as ISO/IEC 17025 for digital testing and laboratory setup, and ISO/IEC 17020:2012 standards for conducting a conformity assessment on the evidence.
There are several branches in digital forensics that play an active role in cybercrime divisions.
As per ISO/IEC 27037 framework, the examiner should adhere to the use of tools validated by the body.
- Data Acquisition,
- Data Validation and verification (V&V),
- Evidence Extraction,
- Data Reconstruction, and
- Documentation.
There are many open-source and proprietary Digital Forensics Tools available in the market such as the Sleuth Kit, FTK Imager, Xplico, osForensics, Winhex, etc.,
What is NIST definition of digital forensics?
Digital forensics is used to identify, collect, protect, preserve, analyze, extract, incident activity, recovery, and document a digital evidence report for cybercrime activities on the victim and criminal offender’s evidence for legal liabilities, civil, administrative, and criminal proceedings. Digital forensic investigation is carried out by law enforcement, and individual and private entities. Throughout the investigation data acquisition, data analysis, data integrity, data extraction, and reporting play a crucial role in the process.
The key characteristics that one should possess to become a successful digital forensics examiner? Anything comes to your mind now?
In the digital forensic field, the roles and responsibilities of a forensic practitioner adhere to the digital service delivery of cybercrimes, security incidents, and other related crimes. This role required several skill sets to achieve high-level forensics examiner experience in capturing, analyzing, and extracting the digital data from the evidence. The following skill sets are requisite to be a forensic practitioner.
✓Investigative strategy
✓Education and experience in Information technology, Cybersecurity, cybercrime, and forensics field.
✓Existing and new forensic Tools and Techniques (T&T).
✓Laws and Industry regulations knowledge.
✓Industry practices.
✓Ethics in professionalism.
✓Emotional intelligence.
✓Competent and problem-solving.
✓Professional certifications in Cybersecurity, digital forensics, and hacking.
✓Subject-matter expert (SME) to the team.
✓Chain of custody.
✓Communications skills.
Introduction:
Since the formation of intellectual property rights. The main purpose and objectives vary from country to country across the globe with consideration such as types are patents, copyrights, trademarks, and trade secrets etc., Our main investigational focus is to examine a USB drive belonging to an employee who left the company and now works for a competitor.
Investigation and Development Procedures:
To conduct internal digital investigations and forensics examinations on company computing systems. Our main investigational focus is to examine a USB drive belonging to an employee who left the company and now works for a competitor.
We have received additional instructions with the keyword “confidential” to look for the documents in the USB drive. In this section, we examine the USB drive to identify any evidentiary artefacts that might relate to this case. All the required procedures such as identifying, analyzing, investigating, developing, and testing various operations are documented with Autopsy, it’s an open-source tool [1].
Hands-On Project 1/Hands-On Project 2/Hands-On Project 3
Assessment Scope:
The assessment scope of the Digital forensic investigations for this case is as follows:
- To analyze the digital media with respect to the evidence on Company Giggig Tech proprietary materials.
- To capture a disk image using “Access Data FTK Imager Lite” for digital forensic investigations.
- To analyze the USB to discover evidence related to M57 Patent Case.
- To discover the metadata using WinHex editor.
- To explore different types of File Headers.
Hands-On Project 1–3
Step 1: First, Open the “Autopsy tool” Home screen window on your PC. As shown in Figure 1.
Step 2: Start Autopsy for Windows and click the Create New Case icon. In the New Case Information window, enter C1Prj01 in the Case Name text box.
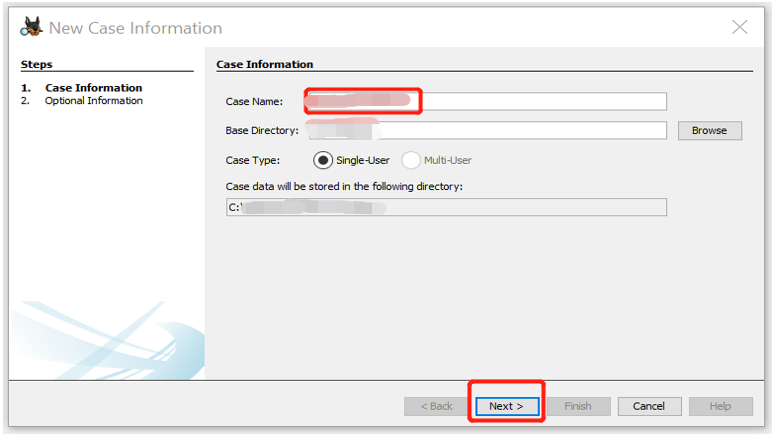
Step 3: Now, Click Browse next to the Base Directory text box. Navigate to and click your work folder, and then click Next.
Step 4: In the Select Data Source window, click the Select data source type list arrow, and click Disk Image or VM file. Click the Browse button next to the “Browse for an image file” text box, navigate to and click your work folder and the C1Prj01.E01 file, and then click Open. Click Next. In the Configure Ingest Modules window, click Select All. Click Next and then Finish.
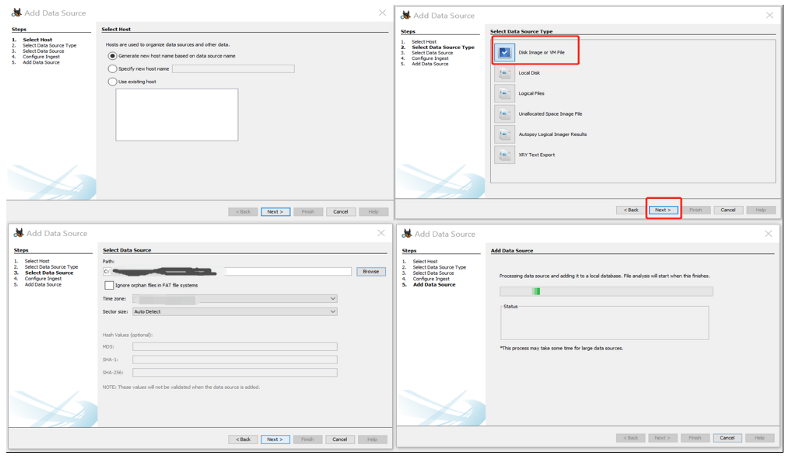 
Step 5: In the Tree Viewer pane, expand Views, File Types, By Extension, and Documents. We examine each subfolder under the Tree pane section to determine which folder might contain files of interest to this case.
Step 6: If you found any files related to the case, select the files as a group, right-click the selection, and click Extract File(s). In the Save dialogue box, click Save to save the files automatically in Autopsy’s case subfolder: Work\Chap01\Projects\C1Prj01\Export.
Step 7 Write a short report of no more than one paragraph in the report, including facts from any content you found. When you’re finished, leave Autopsy running if you’re continuing to the next project.
Conclusion:
In this USB investigation case, we identified and analyzed the seized USB drive for any potential breakthrough in this case. As a result, we successfully extracted the two files (one text file and one Excel sheet). Based on the extracted files from Autopsy, we identified Sylvia left a suicide note as shown in Figure 8. Furthermore, in Figure 9, an Excel sheet briefs about the asset auditing information. Sylvia’s life insurance is valued at $1 million set along with the rest of the assets. That concludes this case is related to a possible murder by her boyfriend to claim the insurance and other assets as a partner.
Hands-On Project 2–2
Investigation and Development Procedures:
To conduct internal digital investigations and forensics examinations on company computing systems.
Our main investigational focus is to examine a USB drive belonging to an employee who left the company and now works for a competitor. We have received additional instructions with the keyword “confidential” to look for the documents in the USB drive. In this section, we examine the USB drive to identify any evidentiary artefacts that might relate to this case.
Step 1: First, Open the “Autopsy tool” Home screen window on your PC. As shown in Figure 1.
Special Note: Please, refer to Hands-on project 1–2, and repeat the same procedures from step2 to step5. To create, browse, select folders and create a workspace, procedures are similar to Hands-on project 2–2.
Step 6: Click the Keyword Search button at the far upper right, type “confidential” in the text box, and then click Search.
Step 7: In the Result Viewer pane, a new tab named Keyword search 1 opens. Click each file to view its contents in the Content Viewer pane.
Step 8: Ctrl + right-click to select the files in the Keyword search 1 tab. Right-click this selection, point to Tag File, and click Tag and Comment. In the Create Tag dialogue box, click the New Tag Name button, type Recovered Office Documents in the Tag Name text box, and then click OK.
In the Create Tag dialogue box, click the New Tag Name button, type Recovered Office Documents in the Tag Name text box, and then click OK.
Step 9: Click Generate Report at the top. In the Generate Report window, click the Results — Excel option button in the Report Modules section, and then click Next.
Step 10: In the Configure Artefacts Report window, click the Tagged Results button, click the Recovered Office Documents check box, and then click Finish.
Step 11: In the Report Generation Progress Complete window, click the Results — Excel pathname to open the Excel report. This Excel file should have several tabs of information about the files you tagged for this project.
Step 12: Write a memo to Ms. Jones, including facts from any content you found, make sure to list the filenames where you found a hit for the keyword. List the cluster numbers for hits that occurred in unallocated space. Include the Excel spreadsheet with the report.
Conclusion:
In this USB investigation case, we identified, and analyzed the seized USB drive for any potential breakthrough in this case. As a result, we successfully extracted the Nine files with the given keyword “Confidential” and generated an Excel sheet.
Based on the extracted files from Autopsy, we identified Ex-Employee taking the company’s confidential and trade secret documents as shown in Figure 8. And Figure 13. Furthermore, an Excel sheet briefs about the Confidential file information to put forward the case legally with the proceedings. That concludes, this case is related to Intellectual property (IP) theft by an Ex-employee and shared with the competitor for grants in exchange.
Hands-On Project 3–3
Investigation and Development Procedures:
To conduct internal digital investigations and forensics examinations on the company’s trade secret theft. Our main investigational focus is to examine a USB drive that was received through an anonymous letter to the HR department belonging to a former employee, Ralph Williams, who left the company and now works for a competitor. We have received additional instructions Ralph Williams to take photos belonging to ACE Sailboats Pvt ltd., that contained trade secrets from April 2006, to look for the Photos in the USB drive which was shared with the new employer Smith Sloop Boats, a competitor of ACE Sailboats. Ms. Olsen specified; another specialist has already made an image of the USB drive in the Expert Witness format (with an . E01 extension). In this section, we need to examine its contents for any photograph files and other artefacts that might relate to this case to justify whether the anonymous complaint is true or a false flag.
Step 1: First, Open the “Autopsy tool” Home screen window on your PC. As shown in Figure 1.
Special Note: Please, refer to Hands-on project 1–2, and repeat the same procedures from step2 to step5. To create, browse, select folders and create a workspace, procedures are similar to Hands-on project 3–2.
Step 6: In the Result Viewer pane, scroll to the right, if necessary, until the Modified Time column is in view. Sort the column by clicking the Modified Time header.
Step 7: Scroll down until you find the first file with a starting month of April 2006, and then click the file to view it in the Content Viewer. Press the down arrow on the keyboard to view all files created or modified in April 2006.
Step 8: Ctrl + Right click every file that has a photo of a boat or part of a boat. Right-click this selection, point to Tag File and then Quick Tag, and click Follow Up.
Step 9: In the Tree Viewer pane, scroll down and expand Tags, Follow Up, and File Tags. In the Result Viewer pane, click the Thumbnail tab to view the tagged photos.
Step 10: To create a report, click Generate Report at the top. In the Generate Report window, click the Results — HTML option button in the Report Modules section, and then click Next.
Step 11: In the Configure Artefacts Report window, click the Tagged Results button, click the Follow-Up check box, and then click Finish.
Step 12: In the Report Generation Progress window, click the Results — HTML pathname to view the report. When viewing the report, click the links to examine the tagged files. When you’re finished, click Close in the Report Generation Progress window.
Step 13: Right-click on the Html Report and Click Open to view the report in detail.
Step 14: Contains thumbnails of images that are associated with tagged files and results.
Conclusion:
In this USB investigation case, we identified and analyzed the USB drive for any potential breakthrough in this case. As a result, we successfully extracted the Thirty-seven files with the given instruction “Photos” and generated an HTML report.
Based on the extracted files from Autopsy, we identified Ex-Employee didn’t take the company’s confidential and Trade secret documents as shown in Figure 15 summary. Furthermore, an Excel sheet briefs about the Confidential file information to put forward the case legally with the proceedings. That concludes, this case is not related to Intellectual property (IP) theft by an Ex-employee, and this claim is a false flag.
— — — — — — — — — — — — — THE END — — — — — — — — — — — —
Thanks for reading! Have a pleasant day!
Quote of the day:
**Growth is often a painful process.**
成長は往々にして苦痛を伴う過程である。
