Photo by Nick Fewings on Unsplash.
There are many topics to cover and boxes to check when adopting secure authentication within your organization — everything from using the right technologies to documenting policies and processes.
In this guide, we take you back to the basics to ensure you’re covering account security from A to Z.
Having the right “tools and rules” for secure authentication in place is as foundational to your organization’s security as learning the alphabet is to your success in school and life.
Achieving strong account security needs to be done sooner rather than later for the health and future of your business.
Data from IBM’s 2021 Cost of a Data Breach Report shows that one-in-five data breaches in 2020 resulted from credential compromise. The average cost associated with this attack vector tops $4.3 million.
This makes sense considering that Verizon’s 2021 Data Breach Investigations Report (DBIR) shows that user credentials are among the most favored data types for cybercriminals to target.
Having a secure authentication framework and the right tools in place helps you:
- Provide a good user experience without sacrificing account security,
- Ensuring only the right people have access to your protected systems and data,
- Protect your network, IT systems and sensitive data against compromise and theft,
- Ensure compliance with industry regulations and standards,
- Save money in terms of remediation costs, non-compliance penalties, and lawsuits.
So, what are the basics of secure authentication that every enterprise needs to have in place? It’s time to review your ABCs…
Access Management
Access management involves everything relating to user identity, authorization, and authentication. Basically, it’s about having mechanisms in place to ensure that only verified (authenticated) authorized users can access your company’s secure digital and physical systems and the data they contain. Some of these protocols include:
- Using access controls to specify who can access what systems and how they can do so;
- Setting policies and procedures for authorizing users and creating accounts; and
- Outlining responsibilities relating to creating and managing user accounts and systems.
Brute Force (and Other Credential Compromise) Attack Protections
The successful compromise of a single user’s credentials can leave your business reeling. Credential compromise attack methods come mainly in two forms — brute force and credential stuffing attacks.
The difference between the two is that brute force is about “guessing” passwords and/or usernames with the hope of finding a match, whereas credential stuffing focuses on trying to match known username-password combinations with the right websites.
Looking for more information on brute force attack prevention techniques? Look no further.
Certificate-Based Authentication (Passwordless Authentication)
There are many ways to enhance the security of account authentication processes. Most of these involve either completing additional steps or providing secondary factors in addition to manually entering a password.
The list looks like acronym soup: SFA, 2SV, 2FA, MFA (more on multi-factor authentication below). However, there is another way to improve authentication security that doesn’t involve using passwords at all — and that’s PKI certificate-based authentication.
Client authentication certificates are digital files that you install on your employees’ devices. They allow users to securely authenticate to your protected web applications and resources without ever having to remember or type passwords.
When you pair it with a trusted platform module (TPM) — which comes with virtually every modern smartphone and computer nowadays — it’s more secure than multi-factor authentication methods on their own.
Certificate-based authentication means stronger security for your organization, a better experience for your users, and fewer password reset requests for your help desk to handle.
Database Security & Management
As more companies move to cloud environments, it’s not uncommon for companies to store user information in online databases.
But if that information isn’t stored securely, it can spell disaster. Virtually every day, new breaches are announced that show companies aren’t taking the necessary steps to secure their databases against unauthorized access.
Here are several ways to make your databases and their contents more secure:
- Restrict database access to only users who require it.
- Manage and update lists of authorized users regularly.
- Encrypt sensitive user data prior to uploading it to the databases (and store the decryption keys separately).
- Secure databases with unique passphrases.
- Store only salted password hashes, never plaintext passwords.
- Use a slow but strong password hashing algorithm for user account password obfuscation.
- Check databases for security misconfigurations.
- Secure your web applications that pull from those databases against SQL injection attacks and other web application attacks (more on that later).
OWASP published a great resource on secure database access that provides additional guidance and recommendations.
Encryption (Data Security)
Another key element of secure authentication for your website and web apps is securing users’ sensitive credentials while they’re in transit. Encrypting those connections is how you can protect those credentials during the login process.
The internet is an insecure public network. Data transmits via the insecure hypertext transfer protocol (HTTP), which means that data transmits from one endpoint to another (from your customer’s browser to your webserver) in a readable format.
But these transmissions don’t occur in a straight line — data transmissions bounce between different routers before reaching their destinations, which means there are plenty of places for bad guys to intercept them along the way.
So, when a user logs in to their account on an insecure website, then their credentials transmit in a way that bad guys can intercept them. (Basically, while they’re bouncing from one router or touchpoint to the next until they reach their intended destination server.)
The way to combat this is to secure your web server using SSL/TLS certificates. These certificates enable users to connect via secure, encrypted HTTPS connections instead. HTTPS encryption secures users’ login information against man-in-the-middle attacks.
Of course, you’ll also want to ensure that account passwords are also secure when they’re at rest as well (i.e., stored in a database). That requires the use of salting and hashing — but we’ll speak more to that in the password security section.
Fundamentals to Avoid Broken Authentication
Broken authentication ranks No. 2 on OWASP’s Top 10 list of web application security vulnerabilities. As the name implies, the term refers to vulnerabilities and misconfigurations within a web app’s authentication and session management processes that result in someone gaining unauthorized access.
To avoid these issues:
- Require strong passwords,
- Prevent users from using default and weak passwords (compare passwords to databases, breach lists, etc.),
- Use multi-factor authentication or a passwordless authentication method,
- Avoid including session IDs in your URLs,
- Harden your web apps against SQL injections, account enumeration attacks, and other server-side attacks, and
- Educate your employees about phishing campaigns, cyber attacks, and client-side attacks.
Check out OWASP’s Authentication Cheat Sheet for a look at some of the basics.
General Best Practices to Keep in Mind
Yes, using “general” is a bit of a cop-out when listing the ABCs of secure authentication. (Matching items up with specific letters is more challenging than you might think!) But we figure this could be an area that we use to cover or address some best practices that didn’t really fit other letters (or specific letters were already in use) in the rest of the article.
-
Limit the length of user sessions. Although users may love to have indefinite session lengths, it’s bad for security. Require users to reauthenticate after a set period.
-
Adhere to industry and regional standards. This is important because you need to ensure your security and authentication measures are compliant with regulatory and regional security requirements.
-
Don’t forget BYOB devices. As more companies embrace remote work capabilities, this is an important item to remember. Set and enforce strict policies relating to the use of personal devices. If an employee’s device gets infected with malware and they use that device to access work-related accounts and resources, then any systems they touch are as good as compromised.
Human Factors
We don’t like to point fingers, but people represent one the biggest vulnerabilities when it comes to account security.
All it takes is one “oops” or an intentionally malicious action for your company to be featured as part of the latest data breach headline. This relates to everything from poor cyber hygiene and password security practices to falling for phishing campaigns and scams.
And much like how there’s no single human-related cause that we can point to for all data breach woes, likewise, there’s no one-size-fits-all cure to this ailment. Minimizing the risks associated with employees and other authorized users requires a multi-pronged approach that includes:
- Educating users to identify and respond to various cyber threats and attacks,
- Creating, implementing, and enforcing security policies, and
- Requiring additional layers of security to verify users’ identities.
Identity Assurance
Identity assurance is a crucial element of secure authentication and risk management because it requires having a way to prove the identity of a person, company, or other entity is legitimate (i.e., they are who they claim to be). Identity assurance is important on both public and private networks:
- If you use an organization validation (OV) or extended validation (EV) SSL/TLS certificate to secure your website, you’re providing customers with a way to check whether your company is legitimate. The certificate offers identity assurance to your customers because a publicly trusted certificate authority (CA). This way, they know they can log in and buy products from your site without having to worry that their data will be stolen.
- Authorized users can log in to secure internal resources using company-issued credentials. Companies that have private CAs can issue client authentication certificates that prove your identity so you can access secure resources.
Not having a way to verify someone’s identity is like receiving a phone call from one of your company’s executives for a last-minute wire transfer.
Maybe the caller legitimately is that executive, but maybe they’re not — the takeaway here is that you need to have a way to know for certain that the caller isn’t a cybercriminal who’s trying to scam you. (Hint: call that person back directly using an official company phone number that you get from your company’s directory. Never call back using a number provided by the caller in question.)
Joint Authorization (Multi-User Approvals)
Assigning and managing user access should never be a one-person job within enterprise environments. Ideally, a good risk management practice for user access entails having different people handle different roles within the process.
For example, the person requesting access shouldn’t be the same person who creates the user profiles or the person who reviews the user access requests for approval.
This delegation of responsibilities requires multiple people to participate in the process of creating and managing users. Why is this necessary? To help to protect your organization from security misconfigurations and rogue employees who may use their power to cause harm.
Key Management & Storage
Managing and protecting your private keys should be one of your top priorities when it comes to secure authentication. If your private cryptographic key isn’t secure, then your SSH or client authentication certificate won’t do you any good.
-
Use a certificate & key management platform so you have full visibility. Keeping authentication keys secure is a critical part of authentication security. If even one of them gets lost or compromised, it means that it represents a threat to your organization and customers. Using a management tool helps you to ensure that you know how many certificates and keys you have, where they are, who’s responsible for them, and when they’re going to expire.
-
Use a trusted platform module (TPM) to protect your endpoint cryptographic keys. This standalone piece of hardware operates separately from your endpoint device’s CPU memory, which means that it won’t be affected by malware or logic-based attempts to compromise it. It’s a tamper-resistant security mechanism that protects your keys against physical attacks as well. If someone tries to deactivate or compromise the TPM, the module will stop the endpoint device it’s attached to from functioning. This ensures that the attacker won’t be able to gain access to your cryptographic keys or other data.
Login Attempt Limitations
Although the process is simple, many companies neglect to limit the number of login attempts allowed within a set period. This account protection method helps protect your web apps and other secure systems from brute force attacks and unauthorized access by limiting the number of times someone can repeatedly attempt to login to an account before being forced to stop. You can set limits either through your organization’s access use policy or by setting rate limits.
Whether you choose to limit failed login limits to three attempts or 10 within a specific amount of time, just be sure to set a limit. For added measure, introduce a time delay for added security (and greater frustration for hackers).
Multi Factor Authentication
Multi factor authentication is a way to bolster the security of users’ accounts by adding another layer to it. It requires users to provide a combination of two or more “factors” — things they know, possess or are inherent to them as human beings — to prove their identities in order to access secure systems.
Examples of these respective factors include:
- Passwords or SMS-based one-time PINs (things you know),
- Cryptographically generated codes from mobile authenticator apps, USB security tokens or smart cards (things you have), and
- Biometrics such as voice samples, facial IDs and fingerprint scans (things you are).
An example of multi-factor authentication is when you try to access your retirement account over the phone. In addition to knowing a specific piece of information (passcode), you must verbally state a specific phrase to provide a voiceprint (a biometric) that confirms your identity.
Network Security
Network security is a critical element of secure authentication and vice versa. If your network is secure, then it helps to keep your servers, databases, and user accounts secure.
Likewise, if you have strong authentication measures in place, it helps to prevent unauthorized access to your network (and everything that connects to it). You need to ensure that only authorized users can access your restricted network.
Network security tools such as gateways, firewalls, intrusion detection systems (IDS) enable you to either restrict access to your network altogether or monitor your inbound and outbound traffic to identify anomalies or potential threats. When it comes to user authentication, some things to look out for include:
- Repeated failed login attempts on multiple accounts by individual IP addresses,
- Login attempts from geographic regions where users aren’t located,
- Traffic to and from known malicious websites and IP addresses.
One-Time PINs (OTPs)
There’s often a bit of confusion when it comes to one-time PINs and account security. This ambiguity often leaves people asking questions like:
- Is an OTP a knowledge or possession factor in MFA?
- Are they a secure identity verification method?
- Is there a better option?
In general, an OTP is a single-use code that you receive as part of the login process. A PIN can come as an SMS text message that you receive on your phone, or it could be a push message that an authentication app on your phone generates and “pushes” as a notification.
- SMS text message OTPs. An SMS-based OTP is considered a knowledge factor because it doesn’t require physical possession of something to know (since you receive it via text message). This is a problem because text messages can be intercepted and your phone number can be stolen via SIM swapping attacks. If a bad guy takes over your phone number, they can receive any SMS-based OTPs your accounts send as identity verification — meaning that they can then use those codes to help them take over your accounts.
- Authenticator app OTPs. An authentication app, on the other hand, is a type of possession factor because it requires you to have physical access to your device. These identity verification apps are tied to your individual device and not your phone number, so they’re not susceptible to SIM swap attacks. And since the apps generate the OTPs on your device (i.e., they’re not transmitted to you), they can’t be intercepted. (The risk here would be if you have malware on your device, but if that’s the case, then you’ve got bigger issues!)
Password Security (For Both Users and Admins)
The topic of password security can be looked at from two important angles: how users practice it on the front end and how businesses handle things on the back end. Some quick examples of common password security best practices for users include:
-
Creating long passwords (or, more accurately, passphrases that include multiple unrelated words),
-
Not reusing or recycling passwords (either on one account or across multiple),
-
Refraining from sharing passwords with others (family members and coworkers alike), and
-
Using a password manager to store their passwords so they only have to remember a master password.
For businesses, strong password security entails having policies and procedures in place to guide their efforts. For example, businesses should never keep plaintext password data anywhere that internal or external users can find it. Instead, only store salted password hashes (digests).
On one hand, hashes are one-way cryptographic functions, meaning that they’re basically irreversible for all intents and purposes. On the other hand, a salt is a unique value that you add to passwords prior to hashing to ensure every password generates a unique hash. The process of salting a password prior to hashing looks like this:
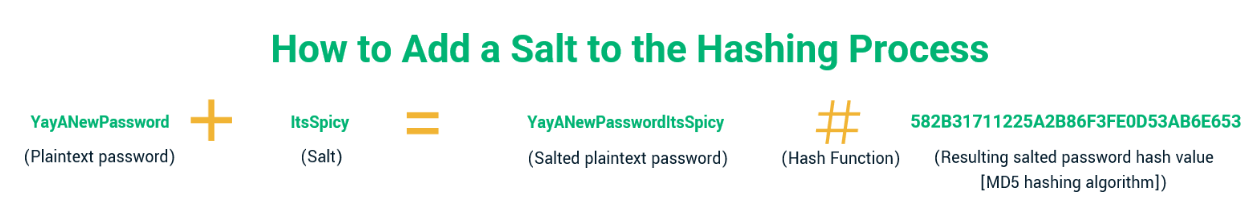If no two passwords have the same hash digest, it makes it virtually impossible for cybercriminals to try to “crack” using hash tables or “chain back” to via rainbow table attacks using today’s technologies.
Question-Style Prompts for User Verification
Everyone knows these prompts — what is your mother’s maiden name? Where did you go to high school? Who did you share your first kiss with? In their special publication (SP 800-63B) on digital identity guidelines, NIST recommends avoiding the use of any of them:
“Verifiers SHALL NOT prompt subscribers to use specific types of information (e.g., “What was the name of your first pet?”) when choosing memorized secrets.”
This statement entails leaving an open-ended field where users can enter their own unique input. The types of information that are commonly asked in those pre-determined fields are the kinds of information that hackers can find online when researching and targeting your users.
Restriction of Access (Principle of Least Privilege)
Regardless of what Jenny and Kenny from Legal say, neither of them needs access to most of your company’s systems. Access privileges aren’t rights, and they should only be granted to people who need them to perform their jobs. Restricting access to select users reduces your organization’s risk exposure.
Ideally, the amount of access should be granted, and it should only be for the duration of the period that a user needs it. For example, if one of your employees is working on a time-sensitive project, they should only be given privileges for that period. Then those privileges should be revoked immediately once they’re no longer needed.
While this may sound like a huge pain in the butt, it’s a lot less burdensome than dealing with the aftermath of a cybercriminal gaining privileged access because an employee fell for a phishing campaign.
Single Sign On (SSO)
Another category of authentication mechanisms that many enterprises consider is single sign on, or SSO for short. It’s a form of password management that allows users to log in once to access multiple systems or web applications during a session.
The benefit of this approach to authentication is that a user can authenticate across multiple systems without having to juggle multiple sets of usernames and passwords. It’s a one-and-done login requirement for the entire session regardless of whether they’re accessing one resource or 10.
Google is a popular example of SSO. Whenever you log in to your Gmail account, you’re automatically also logged in to Google Ads, YouTube and other Google-related services and apps. It’s convenient because users don’t have to remember individual login credentials for each platform and they’re automatically logged in when they go from one to the next.
SSO is great for businesses whose employees practice strong cyber security hygiene and password security best practices. But this approach isn’t without risk, as some experts argue that it creates a single point of failure. Should a user’s credentials become compromised, it means that an attacker will have access to all of the systems those credentials touch.
This is where that PoLP that we talked about moments ago comes into play to reduce your organization’s risk exposure. You’ll need to weigh the advantages and disadvantages of SSO to see if it’s a good fit for your organization.
Train and Educate Your Employees
We touched on this earlier, but your organization’s cyber defenses are only as strong as its human elements. If your employees don’t understand how to identify cyber security threats and the risks associated with them, the center can’t hold, and your defenses will ultimately buckle. Education and training play integral roles in preventing this security failure in authentication and other areas of cyber security:
- Train employees to follow password security best practices and create secure passphrases instead of passwords.
- Require them to use virtual private networks (VPNs) when logging in remotely.
- Use examples of real phishing emails, websites, and remote desktop access scams to illustrate how convincing and realistic cyber attackers’ methods are.
- Share news reports about cyber attacks and data breaches to drive home the importance of practicing strong cyber hygiene.
- Carry out regular phishing tests to see whether your users are applying what they learn and to identify knowledge gaps.
- Update or focus your future training sessions to address those areas of concern.
Updates and Patch Management
You can have the strongest passwords and security tools in place, but they won’t help if you fail to keep your applications, endpoint devices and other IT systems updated and patched. Cybercriminals don’t need to phish or brute force their way into your network if you leave the door open by having unpatched vulnerabilities.
Applying patches and other updates is one of the most basic aspects of cyber security, yet many companies neglect to apply updates until it’s too late. This can result in situations like what we saw in the WannaCry attacks in 2017, when hackers exploited known and patched vulnerabilities in legacy Windows operating systems.
The best way to avoid vulnerability exploits is to apply updates and security patches as soon as they’re available. You can do this manually or by enabling automatic updates.
Vulnerability Management
Vulnerability management and secure authentication go together like burgers and beer. Vulnerability management boils down to identifying, prioritizing, mitigating and reporting vulnerabilities that would otherwise leave your IT systems unprotected. By mitigating these weaknesses in your endpoints, applications, networks and other systems, you’re making everything more secure.
Likewise, protecting your systems from unauthorized access also helps to mitigate vulnerabilities that can lead to future cyber attacks and data breaches.
Work-From-Home Access (Remote Access Security)
Nowadays, people are accessing your network and secure systems from locations outside the office. This is where having remote access security measures plays a key role in keeping your network secure.
- Educate employees on the dangers of phishing and connecting to insecure public networks,
- Require users to connect remotely using a virtual private network (VPN),
- Install PKI certificates your employees can use to authenticate (in lieu of passwords),
- Run antivirus and anti-malware solutions on all endpoint devices to protect them against credential-stealing malware,
- Allow users to login to your secure resources using PKI-based instead of traditional login credentials, and
- Implement zero trust policies and procedures (more on that momentarily).
XSS & Other Web App Vulnerabilities
Cybercriminals use cross-site scripting (XSS) and SQL injection attacks to exploit vulnerabilities that exist within your web application systems. Cybercriminals use XSS attacks (i.e., client-side attacks) to steal session cookies to bypass authentication measures to gain unauthorized access to a user’s account. Basically, this gives the attacker all of the access and capabilities that they have according to their account permissions and privileges.
However, if attackers want to attack your server instead, they can input SQL queries to add, modify, or pull info from your database. Some of the sensitive data they can pull are usernames and passwords, including privileged users such as admins.
To make your web applications more secure against these types of attacks, OWASP recommends the following in their Cross Site Scripting Prevention and SQL Injection Prevention cheat sheets.
You (The Collective “You” of Your Organization)
It’s no secret that good cyber security and account security aren’t just IT initiatives. The importance of having strong security should be an organization-wide priority that’s promoted and supported by company leaders. This includes:
- Company-wide messaging about account security,
- Enforcing security-related policies and procedures, and
- Requiring all users to undergo regular cyber awareness and security training.
Zero Trust
The concept of zero trust is quite simple: never trust anyone or anything automatically, and always verify their identities.
What this means is that no one or thing — not your CEO, IT admin, devices or applications — is trusted automatically. Rather, the identity of each person or machine requesting access to your secure resources must be validated regardless of whether the request originates on your internal or external network.
IBM’s 2021 Cost of a Data Breach Report shows that companies that adopted a zero-trust approach had lower average breach costs ($3.28 million) than those that didn’t ($5.04 million).
